I asked my girlfriend to write down a list of specific things she'd like for her birthday... : r/funny
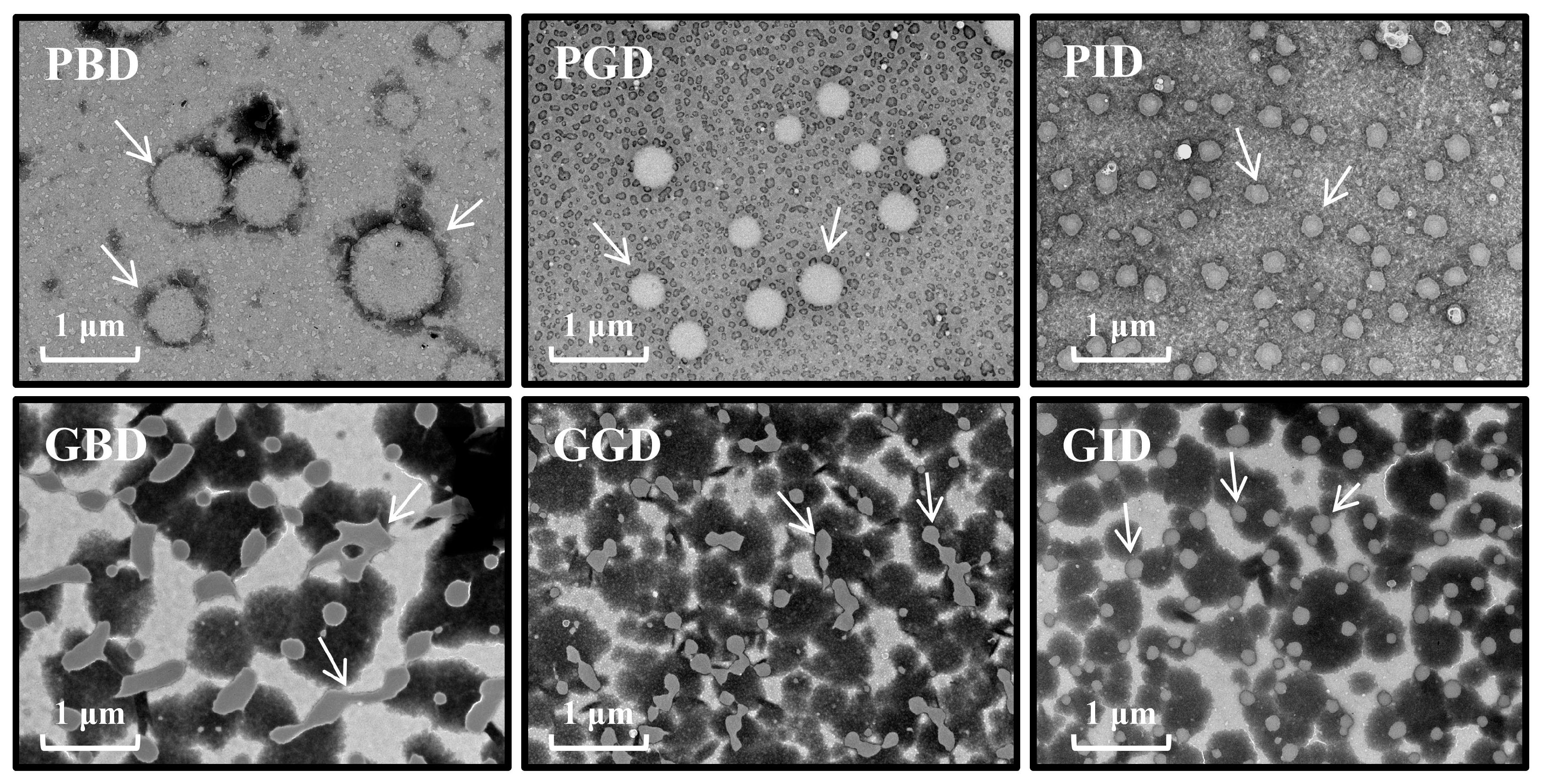
Foods | Free Full-Text | Comparative Study on Hydrolysis, Physicochemical and Antioxidant Properties in Simulated Digestion System between Cooked Pork and Fish Meat

A Back Propagation Neural Network with Double Learning Rate for PID Controller in Phase-Shifted Full-Bridge Soft-switching Power Supply | SpringerLink

web scraping - How to extract name from html text that is covered by hyper link, using lxml Python - Stack Overflow

Verifiably secure fast group authentication protocol with anonymous traceability for Internet of vehicles

Crash when initializing app built and run from Ubuntu 20.04 - #20 by Atabak - Development - 3D Slicer Community